Lab 1
Scenario: Security has been alerted that this computer may have been possibly compromised. We need to answer the below questions.
This lab will be fairly simple with the intention to make them more elaborate.
Lab Setup
Grab Kape output and parse Sysmon event log with my PowerShell script or any other way you like. Link to my script: https://gist.github.com/medmondson44
See prior post for files.
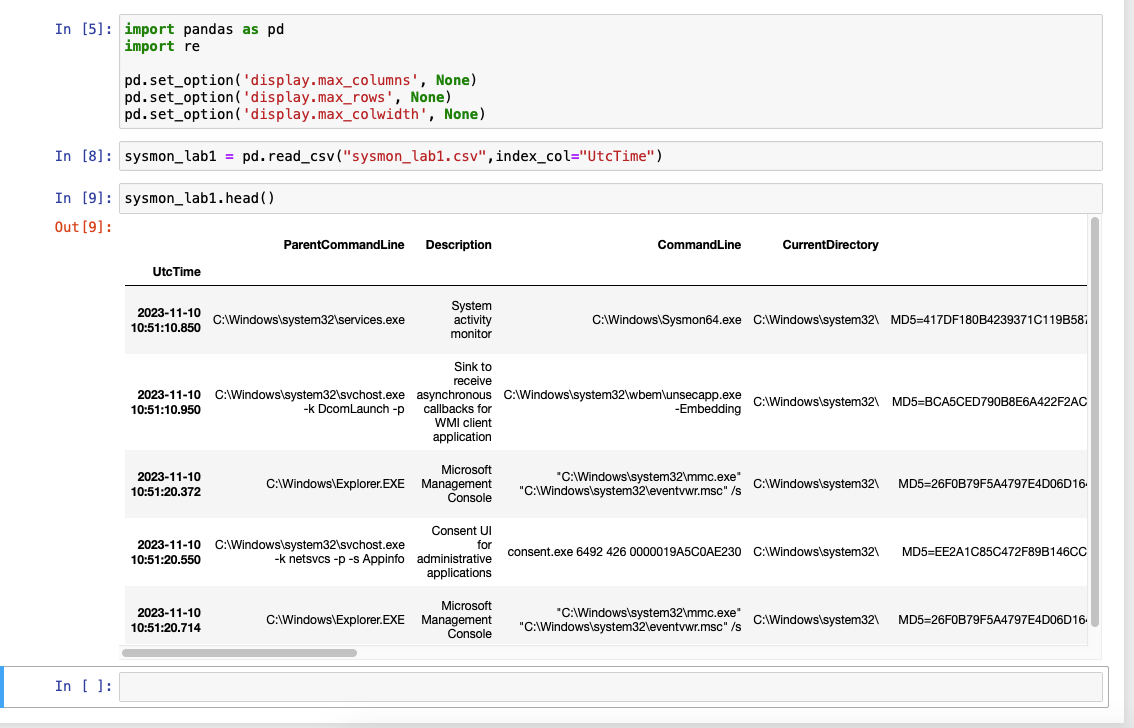
Here I am using the Python library pandas to import the output from the PowerShell script.
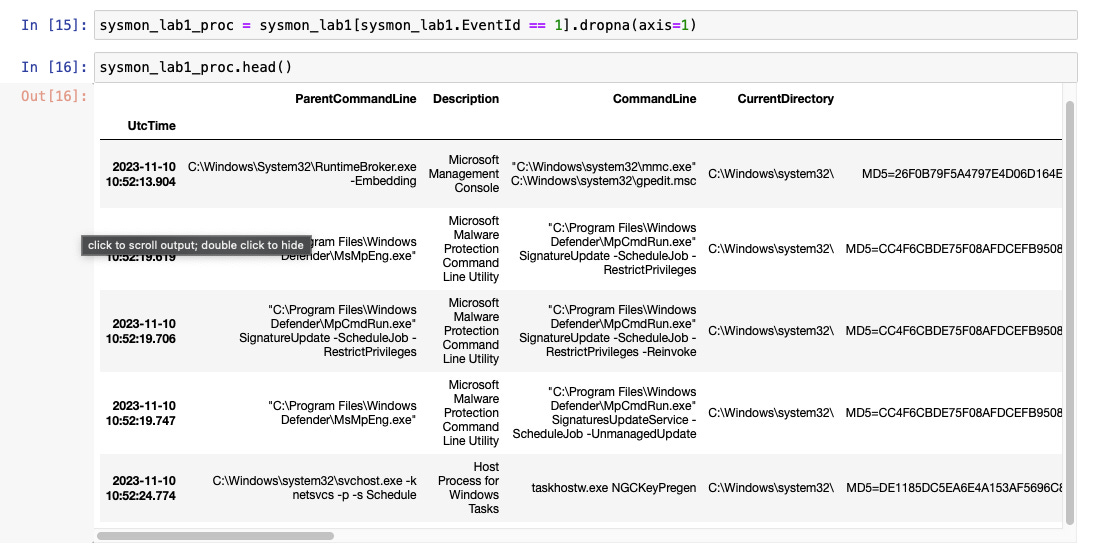
Carve out ProcessCreate logs into a new DataFrame
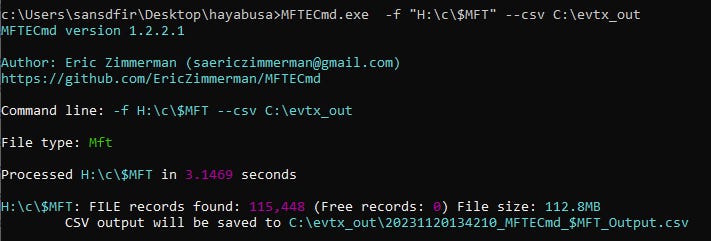
Parse MFT record with MFTEcmd from Eric Zimmerman
Parse Prefetch with PECmd from Eric Zimmerman
1. What is the malicious executable?
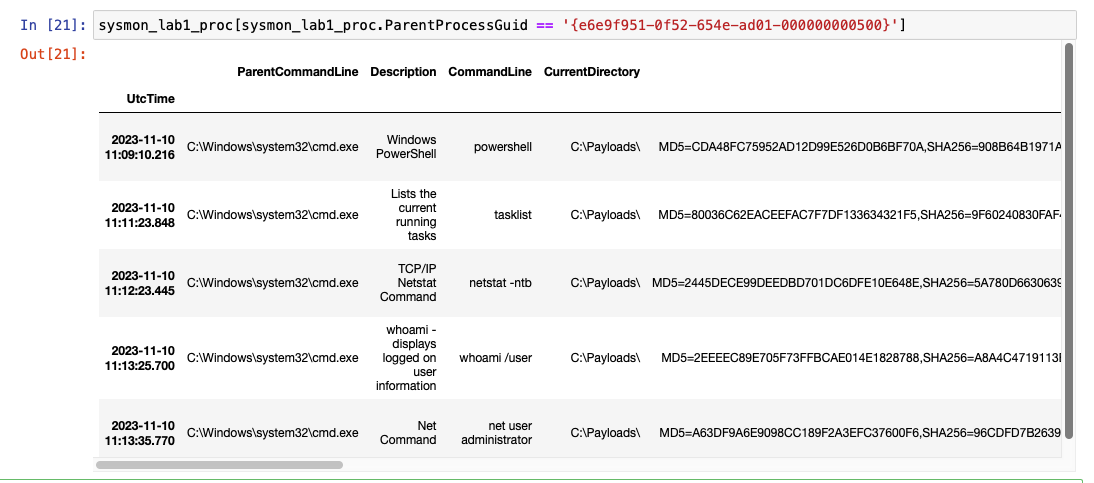
The malicious executable in this scenario was pscp.exe. This was the chain I used to find it. I saw a whoami command which is not normal for my environment.
Then analyzed what the Parent that ran it and continued down the chain.
2. What process did the malicious executable migrate to?
Process migrated into Explorer, I used CreateRemoteThread events to find this.
3. Were any situational awareness commands run? If so what were they.
Yes
4. Which IP and port is the malicious executable communicating with?
You could have used Sysmon ID 3 for network connections or used the MFT like below by looking at it around the time pscp executed.